15
+
YEARS OF
EXPERIENCE
1000
+
SUCCESSFUL
Projects
80
+
Satisfied
Clients

In today’s cybersecurity landscape, maintaining a high Microsoft Defender Score is crucial for organizations striving to strengthen their security posture. The Defender Score offers valuable insight into how well your habitat adheres to recommended security practices. Improving this score not only mitigates risks but also enhances compliance and operational resilience. This blog post explores effective strategies to elevate your Defender Score, providing actionable IT solutions tailored to professional environments seeking advanced threat protection.
How to Improve Defender Score Through Thorough security Assessment
Microsoft Defender score offers a quantifiable measure of your organization’s security configuration based on best practices and threat detection capabilities. To begin improving your Defender Score, start with a thorough security assessment that identifies gaps in policies, device compliance, and threat response workflows. This assessment should include evaluating user privileges, endpoint protection settings, and cloud workload security configurations. Ensuring devices are onboarded to Defender for Endpoint with all detection features enabled is fundamental.
Equally vital is reviewing and implementing recommended security baselines released by Microsoft, which are regularly updated to reflect emerging threats. Adopting zero-trust principles during this phase helps tighten access controls and reduce attack surfaces. Moreover, configuring automated investigation and remediation processes accelerates incident response and directly impacts your Defender Score positively. Collaborating with experienced IT service providers like TechCloud IT Services L.L.C can augment this process through expert guidance and robust orchestration of security tools. Proactively addressing these factors lays a strong foundation for sustained improvement in Defender Score.







How to Improve Defender Score by Optimizing Endpoint Security and policy Management
Optimizing endpoint security is a critical driver in boosting your Microsoft Defender Score. Organizations must deploy consistent policies across all endpoints, including desktops, laptops, mobile devices, and servers. Utilizing Microsoft Endpoint Manager to enforce compliance policies ensures uniform protection and reduces vulnerabilities created by misconfigurations. Policies involving attack surface reduction rules, request control, and exploit protection must be meticulously tailored to the organizational environment.
Beyond policy enforcement, maintaining timely patch management substantially influences defender Score. Vulnerabilities arising from unpatched systems diminish your overall protection efficacy. Automated patch deployment, alongside regular security updates, ensures endpoints remain resilient against evolving threats. Equally, leveraging advanced threat analytics and behavioral monitoring empowers IT teams to detect anomalies early and remediate them before escalation.
Challenges in optimizing endpoint security often revolve around balancing user productivity with strict security constraints. Overly restrictive policies might hinder workflows, while lax controls open doors to exploits. Addressing this requires informed customization underpinned by continuous monitoring and feedback loops, something Cloud Technologies excels at through its managed IT services. Investing in training programs to raise employee security awareness complements technical controls and creates a culture of vigilance, ultimately reflecting in an improved Defender score.
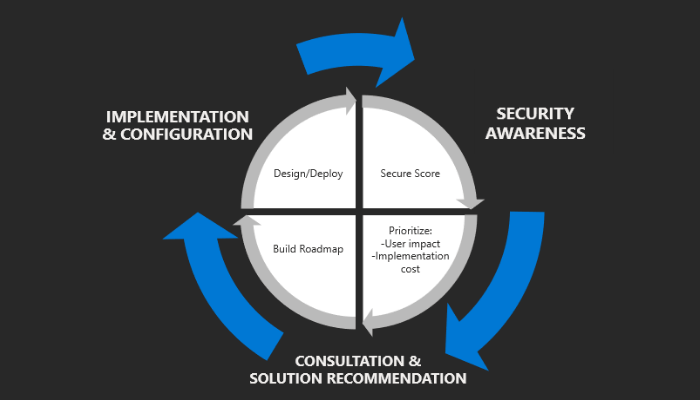
Effective endpoint policy management, combined with proactive patching and user education, form the cornerstone of a resilient security framework. By centralizing control and equipping teams with actionable insights, organizations can systematically elevate their Defender Score and reduce incident response times.
How to Improve Defender Score Leveraging Automation and Continuous Monitoring
Automation and continuous monitoring are pivotal in achieving and maintaining a superior Microsoft Defender Score. Manual configurations and reactive security measures are no longer sufficient in today’s dynamic threat environment. Integrating automation frameworks within Defender for Endpoint allows organizations to streamline threat detection, investigation, and remediation workflows. For example, enabling automated investigation triggers enables swift analysis and remediation of alerts without waiting for human intervention, significantly reducing dwell time.
Continuous monitoring is equally vital for maintaining high visibility across hybrid infrastructures. Deploying SIEM (Security Information and Event Management) systems that ingest and analyze Defender telemetry feeds ensures real-time threat intelligence is actionable. These insights illuminate trends and anomalies, guiding security teams to deploy targeted countermeasures and governance improvements. Challenges in this area often include managing alert fatigue and ensuring the accuracy of automation playbooks – areas where partnering with specialists like TechCloud IT Services L.L.C offers a practical advantage.
Real-world case studies consistently demonstrate that organizations employing automation and continuous monitoring frameworks realize faster threat containment, reduced operational overhead, and an incremental increase in their Defender Score. This strategic approach transforms endpoint protection from a reactive function into a proactive security asset, firmly positioning your organization ahead of emerging cyber risks.

answer time
satisfaction
score
on initial call
same business
day
Elevate Your Cybersecurity Posture by Maximizing Defender Score Benefits
Improving your Defender Score is more than a metric-its an ongoing commitment to fortify your organization’s security framework against elegant cyber threats. By conducting comprehensive assessments, optimizing endpoint policies, and embracing automation with continuous monitoring, IT leaders can achieve measurable improvements and heightened security resilience. Working with expert partners like cloud Technologies (TechCloud IT Services L.L.C) ensures you benefit from tailored strategies, best-in-class tools, and unmatched support.
Whether enhancing compliance, reducing remediation times, or empowering your security operations center, the defender Score is a valuable compass guiding your cybersecurity journey. To initiate your change and discover how to strategically improve your Defender Score, we invite you to connect with us. Our team is ready to deliver solution-focused assistance that aligns with your unique business needs and security mandates.


