15
+
YEARS OF
EXPERIENCE
1000
+
SUCCESSFUL
Projects
80
+
Satisfied
Clients

In today’s rapidly evolving cybersecurity landscape, migrating to a more robust Security Operations Center (SOC) tool is crucial for businesses aiming to enhance threat detection and response capabilities. Microsoft Sentinel offers a powerful, cloud-native solution designed to unify security data and provide advanced analytics. As organizations consider Moving to Sentinel SOC tool, understanding its integration potential, scalability, and operational benefits is key to maximizing security posture. This article explores why transitioning to Sentinel is a game-changer for IT security teams.
Understanding the Value of Moving to Sentinel SOC Tool
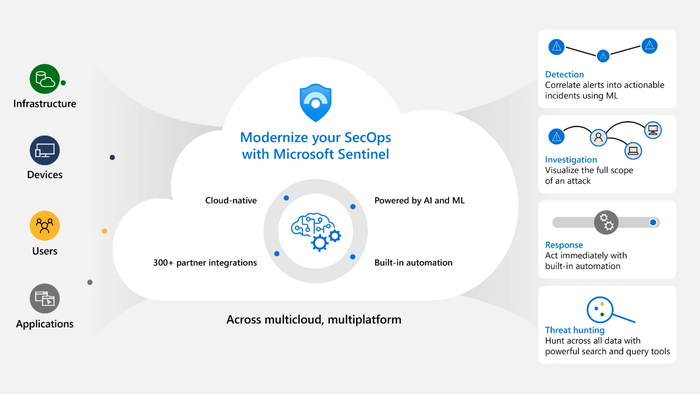
Migrating to the Microsoft Sentinel SOC Tool marks a strategic upgrade for organizations looking to streamline their security operations. Sentinel is a cloud-native SIEM (Security Information and Event Management) and SOAR (security Orchestration Automated Response) platform that allows security teams to collect data across an enterprise’s entire digital infrastructure – including users, applications, servers, and devices running on-premises or in any cloud. This unified data platform enables real-time threat detection and remediation through AI-driven analytics and automation.
For companies transitioning from legacy SOC tools or on-premise systems, Sentinel reduces the complexity of managing disparate security solutions by centralizing alerts and events on a scalable platform. Its integration with Microsoft 365, Azure, and hundreds of other third-party apps allows for seamless ingestion of telemetry and logs. This enables faster identification of potential breaches and reduces noise with intelligent prioritization of high-risk incidents.
Moreover, with a pay-as-you-go pricing model, Sentinel offers cost efficiency, enabling organizations to optimize resources without ample upfront investments. The native automation capabilities cut down manual tasks and incident response times, empowering SOC analysts to focus on strategy rather than firefighting. Moving to Sentinel SOC Tool unlocks a more proactive, adaptive, and extensive security framework – essential for today’s evolving cyber threat habitat.







Key Benefits and Challenges of Moving to Sentinel SOC Tool
Migrating to Microsoft Sentinel presents numerous advantages, but organizations should also be aware of potential challenges to ensure a smooth transition. One of the most significant benefits is Sentinel’s cloud-native architecture, which eliminates the need for costly infrastructure management. This agility allows IT teams to elastically scale resources based on demand, seamlessly accommodating growth or fluctuations in security event volume.
Sentinel’s built-in AI and machine learning analytics drastically improve threat detection accuracy by correlating signals across multiple sources and identifying anomalies that may or else be missed. This leads to quicker incident analysis and reduces false positives, which are a common pain point for SOC teams. The platform’s SOAR capabilities automate routine response actions, such as blocking IP addresses or isolating compromised devices, thereby accelerating containment and remediation efforts.
Another advantage is Sentinel’s extensive integration ecosystem, allowing customization to fit diverse enterprise environments. Whether integrating with custom apps or established security tools, Sentinel supports flexible connectors and APIs for smooth data ingestion and workflow automation.
However, organizations may face challenges during migration, such as data normalization complexities when consolidating logs from various legacy systems. There is also a learning curve associated with Sentinel’s query language, Kusto Query Language (KQL), which requires analyst training to exploit the platform’s full analytical potential. Additionally, migrating past data to Sentinel can pose technical and cost challenges that require careful planning.
To overcome these obstacles, Cloud Technologies-operating as TechCloud IT Services L.L.C-provides expert guidance on best practices for migration, including phased adoption strategies, staff training, and custom integration solutions. Partnering with a trusted IT service provider ensures you harness all the benefits while minimizing risk and disruption to current security operations.
Embracing Microsoft Sentinel demands both technical readiness and strategic foresight. By actively engaging experienced professionals during migration, organizations can ensure optimized configuration and user adoption, laying the groundwork for sustained SOC excellence. With careful planning, the transition becomes an opportunity to not only upgrade technology but also elevate security operations across the board.
Practical Considerations When Moving to Sentinel SOC Tool
When planning a move to Microsoft Sentinel, several practical elements should be addressed to ensure a successful deployment. First, it is essential to map out the current security data sources and identify which logs and telemetry will be ingested into Sentinel. This includes configuring connectors for Azure resources, on-prem infrastructure, network devices, and third-party cloud services. Establishing a comprehensive data ingestion strategy guarantees a more complete threat visibility.
Second, organizations need to develop incident response playbooks leveraging Sentinel’s automation capabilities. These playbooks help SOC teams standardize responses to common threats and speed up detection-to-remediation cycles. Incorporating customized alerts and tuning detection rules based on organizational risk profiles further refines operational efficiency.
Additionally, leveraging Sentinel’s analytics tools means SOC analysts should become proficient with Kusto Query Language (KQL). Investing in training ensures the team can build tailored threat-hunting queries and identify subtle patterns indicating advanced persistent threats (APTs).
A noteworthy case study involves a financial services firm that engaged Cloud Technologies to transition from a fragmented on-prem SIEM to Microsoft Sentinel. The engagement included data migration, connector integration, and automation playbook growth. Post-migration, the client reported a 40% reduction in incident response times, improved threat detection capabilities, and significant cost savings on licensing and hardware.
By engaging with knowledgeable service providers like TechCloud IT Services L.L.C, organizations can navigate common challenges such as data normalization and querying complexity smoothly. Ultimately, these considerations make moving to Sentinel an operational upgrade that drives measurable improvements in security resilience.

answer time
satisfaction
score
on initial call
same business
day
Unlocking the Future of Security Operations with Sentinel
Transitioning to Microsoft Sentinel is more than a technological upgrade-it’s a strategic move toward a modern, efficient, and proactive Security Operations Center. As cyber threats become increasingly refined, having a scalable and intelligent platform to centralize threat detection and automate response is imperative. By moving to Sentinel, businesses gain enhanced visibility, streamlined operations, and the ability to act decisively against cyber adversaries.
At TechCloud IT Services L.L.C, trading as Cloud Technologies, we specialize in guiding enterprises through a tailored migration journey designed to minimize disruption and maximize security benefits. Whether you are just beginning to explore Sentinel or ready for deployment, our experts provide end-to-end support-from consulting and planning to implementation and training.
If you’re ready to advance your security posture and harness the power of a cloud-native SOC platform, we invite you to connect with us. Together, we can build resilient defenses that keep your data and infrastructure safe in today’s complex digital environment. Visit our contact page to learn more and initiate your transition to Microsoft Sentinel SOC Tool today.
Contact us for customized solutions and expert assistance.


