Services
Cloud Technologies - getting
IT done.

Sentinel Integration with Google: Transforming Cloud Security Operations Microsoft Sentinel integration with Google platforms establishes a powerful synergy that elevates cybersecurity postures for organizations. Sentinel’s advanced SIEM functionalities, including AI-driven threat detection, automated response workflows, and real-time analytics, complement Google Cloud’s rich data ecosystem. This integration enables seamless ingestion of logs and events from Google […]
Read this post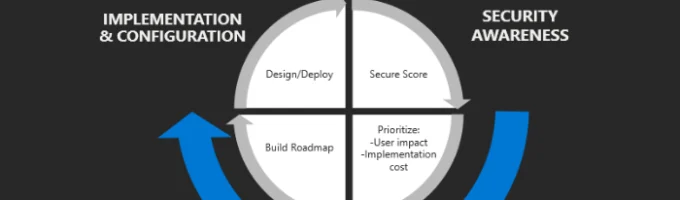
Understanding the Impact of Defender Score Improvements on Security Posture Improving your Microsoft Defender Score is more than just a metric-it reflects the robustness of your security strategy and operational readiness against cyber threats. The Defender Score, part of Microsoft secure Score, evaluates your organization’s security configuration and activity, assigning points based on the implementation […]
Read this post
Understanding the Pros and Cons of MSPs in Dubai’s Dynamic IT Market Dubai’s fast-paced business surroundings has led to a surge in demand for Managed Service Providers that can streamline IT operations. on the positive side, MSPs offer businesses access to cutting-edge technologies without the ample investment typically required to build an internal IT department. […]
Read this post
Unlocking the Potential of Microsoft Modern Workplace for Business Transformation The Microsoft Modern Workplace is more than just a set of tools-it represents a strategic framework that transforms traditional business operations into fully integrated, agile systems optimized for today’s workforce. At its core, this approach consolidates Microsoft 365 services such as Teams, SharePoint, OneDrive, and […]
Read this post
Unlocking Growth Opportunities: Benefits of Microsoft Digital Transformation Microsoft digital transformation provides a complete framework that enables businesses to harness technology for accelerated growth and operational excellence. By embracing Microsoft’s ecosystem-including Azure cloud services, Microsoft 365, Dynamics 365, and Power Platform-organizations can streamline workflows, improve data-driven decision-making, and foster collaboration across distributed teams. These tools […]
Read this post
Achieving Compliances through SOCaaS: An Integrated Approach to Regulatory Adherence Compliance is no longer a checkbox exercise but a fundamental aspect of organizational resilience and customer trust. SOCaaS offers an integrated approach to achieving compliance by leveraging continuous monitoring, automated reporting, and expert incident response tailored to regulatory requirements. At its core, SOCaaS centralizes security […]
Read this post
What Makes Data Center Network hosting Essential for Modern Enterprises Data center network hosting is basic for enterprises that require uninterrupted access to applications, data, and cloud platforms. Essentially, it involves provisioning and managing connectivity infrastructure within a data center that facilitates seamless interaction between servers, storage systems, and external networks. The network infrastructure must […]
Read this post
Comprehensive IT Services for Modern Businesses Efficient IT services encompass a vast array of solutions designed to meet the diverse needs of contemporary organizations. From infrastructure management and cloud computing to cybersecurity and help desk support, these services are critical in maintaining operational continuity and enhancing competitive advantage. Cloud Technologies specializes in comprehensive IT service […]
Read this post
Unlocking Business Potential with UAE Based cloud security Outsourcing Outsourcing cloud security in the UAE has rapidly evolved from a tactical solution into a strategic imperative for many enterprises. UAE based Cloud Security Outsourcing entails partnering with specialized IT firms like TechCloud IT Services L.L.C-operating under the trade name Cloud Technologies-that offer comprehensive security services […]
Read this post
Unlocking Enhanced Security Through Sentinel Integration with Microsoft Solutions Microsoft Sentinel serves as a cloud-native Security Information and Event Management (SIEM) and Security Orchestration Automated Response (SOAR) platform designed to unify threat detection, investigation, and response across your digital infrastructure. Integrating Sentinel with Microsoft environments such as Azure, Microsoft 365, and the broader Microsoft Security […]
Read this post
Understanding the 24/7 IT Support Calculator and It’s Role in Business Continuity The 24/7 IT Support Calculator is a powerful tool designed to help businesses estimate the cost and extent of around-the-clock IT support services required to maintain seamless operations. By evaluating factors such as system complexity, number of users, infrastructure scale, and anticipated incident […]
Read this post
Understanding IT Support Packages for SME: Tailored Solutions for business growth Small and medium-sized enterprises face unique challenges when managing their IT infrastructure. Unlike larger corporations with dedicated IT departments, SMEs frequently enough require flexible, cost-effective support that can adapt to their evolving needs. IT support packages for SMEs are designed to bridge this gap […]
Read this post
Why Outsourced SOC in UAE Is a Strategic Cybersecurity Move Managing cybersecurity internally can strain IT teams, especially given the increasing complexity of cyber threats. Outsourced SOC in UAE offers a practical solution by providing expert monitoring and incident response capabilities around the clock, without the overhead of building an internal SOC from scratch. This […]
Read this post
Breaking Down the Average Cost of IT Support Services Determining the average cost of IT support involves evaluating diverse pricing structures tailored to various business requirements. Typically, IT support can range from hourly rates to fixed monthly fees, depending on the scope, complexity, and delivery mode of services. For small to medium enterprises (SMEs), monthly […]
Read this post
Comprehensive Overview of Fully Managed Office 365 Support Fully managed Office 365 support is a holistic service designed to oversee all aspects of Microsoft Office 365 deployment, maintenance, and optimization. This service encompasses proactive monitoring, user management, security enforcement, and troubleshooting tailored to your business needs. At Cloud Technologies, trading as TechCloud IT Services L.L.C, […]
Read this post
Understanding the Core Features of Meraki Network Security Meraki network security revolves around a holistic, cloud-managed platform that integrates multiple security layers, simplifying complex network defense mechanisms. At its foundation is Cisco Meraki’s dashboard, which provides real-time visibility and granular control over all network devices, including firewalls, switches, wireless access points, and endpoint security. This […]
Read this post