Services
Cloud Technologies - getting
IT done.

Comprehensive Entra ID Server IT Support for Enhanced Identity Management Entra ID Server IT Support focuses on delivering professional assistance for Microsoft’s advanced identity and access management solution. Entra ID, formerly known as Azure Active Directory, serves as the backbone of secure authentication across cloud and on-premises environments. Our support services encompass installation, configuration, and […]
Read this post
Planning for SOC Integration Best Practices: Foundations for Success Effective SOC integration begins with extensive planning that aligns security objectives with business goals. Organizations must conduct a thorough assessment of their existing IT infrastructure, security tools, workflows, and personnel capabilities. This foundational step identifies gaps and redundancies that could hinder SOC efficiency. Mapping out data […]
Read this post
Complete Network Design Consulting for Optimized IT Infrastructures Network Design Consulting is a specialized service focused on creating network architectures that align with a business’s operational goals and technology needs. Our team at Tech Cloud IT Services L.L.C. brings extensive experience in evaluating current systems, identifying bottlenecks, and recommending scalable, secure network solutions. This process […]
Read this post
Understanding the Dubai IT Support Calculator: A Key to Smarter IT Management The Dubai IT Support Calculator is a specialized resource designed to help businesses in the UAE evaluate their IT support needs accurately. By inputting various parameters such as the number of users, devices, network complexity, and required support levels, companies receive a tailored […]
Read this post
Understanding the Sumo Logic to Sentinel SOC Migration Journey Migrating from Sumo Logic to Microsoft Sentinel represents a strategic shift in how organizations manage security operations and threat intelligence. Sumo Logic is a robust cloud-native platform known for log management and analytics, but Sentinel, as Microsoft’s cloud-native SIEM and SOAR solution, offers extended capabilities that […]
Read this post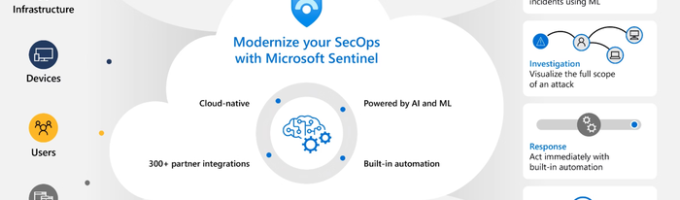
Understanding Sentinel Integration with Azure: A Strategic Cybersecurity Approach Microsoft Sentinel, as a cloud-native security information and event management (SIEM) solution, is designed to seamlessly integrate with Azure environments. By embedding Sentinel into Azure, organizations gain unified visibility across their cloud and on-premises workloads. Sentinel integration involves connecting Azure resources, such as Azure Active Directory, […]
Read this post
Empowering Business Growth Through a Cloud-First Strategy By adopting a Cloud First Digital Transformation framework, enterprises gain the flexibility to modernize legacy systems, streamline workflows, and accelerate time-to-market. This model empowers organizations to leverage advanced technologies such as AI, analytics, and automation directly within cloud environments—driving smarter decision-making and enhanced customer experiences. Furthermore, cloud-native architectures […]
Read this post
Understanding Microsoft Sentinel Implementation Cost: Key Components and Considerations Implementing Microsoft Sentinel extends beyond just licensing fees; it involves a multi-dimensional cost structure shaped by data ingestion volumes, customization, integration requirements, and ongoing management. At its core, Sentinel’s pricing model is consumption-based, meaning that the volume of data ingested directly impacts the monthly charges. Organizations […]
Read this post
Understanding Cloud Security Cost and Licensing: Key Components and Models Managing the cost and licensing of cloud security involves a multi-faceted approach, notably as organizations migrate critical assets to cloud infrastructures. Cloud security expenses are influenced by factors such as the scale of usage, types of security tools deployed, and vendor licensing frameworks. Typically, cloud […]
Read this post
Understanding Remote Hands Support Services and Their Role in IT Operations Remote Hands Support Services refer to a suite of physical support tasks executed on behalf of an organization’s IT team at remote sites such as data centers or server rooms. When internal staff cannot be physically present onsite, these specialized services enable businesses to […]
Read this post
An Overview of IT Function Management Outsourcing: Empowering Business Agility Outsourcing IT function management involves delegating various IT responsibilities-ranging from network management to software maintenance and user support-to an external service provider. This strategic partnership allows enterprises to access cutting-edge technology, skilled professionals, and industry best practices without the overhead associated with maintaining an extensive […]
Read this post
Understanding Security Compliance and Accreditation in Modern IT Environments Security compliance and accreditation represent the structured processes and formal certifications that confirm an organization’s adherence to predefined security policies and regulatory requirements. Compliance involves aligning company practices with laws and standards such as GDPR, HIPAA, ISO 27001, or NIST, ensuring data privacy, risk mitigation, and […]
Read this post
Empowering Digital Growth Through IT Transformation Consultancy in Dubai Navigating the realm of IT transformation consultancy in Dubai requires a comprehensive approach that combines innovation, strategy, and technology adoption. At its core, IT transformation consultancy helps businesses redesign their IT infrastructure and processes to improve agility, reduce costs, and enhance service delivery. With Dubai’s rapid […]
Read this post
Why Choose a Local Managed Service Provider for Your IT Needs? A Local Managed Service Provider serves as an extension of your internal IT team, offering thorough management of your technology environment. Unlike larger, remote MSPs, local providers deliver on-site support and personalized service, which is crucial for resolving issues swiftly and minimizing downtime. they […]
Read this post
What Is a Security Operation Center Calculator and Why It Matters? A Security operation Center calculator is a strategic tool designed to assist organizations in determining the appropriate scale, staffing levels, and budget for their SOCs. As cyber threats become increasingly complex, the demand for a well-equipped SOC grows proportionally. However, blindly investing without precise […]
Read this post
Understanding GDPR and ICO Security Compliance Frameworks The General Data Protection Regulation (GDPR) is a complete privacy law enacted by the European Union that governs how organizations collect, process, and store personal data of EU citizens. It mandates stringent requirements such as lawful data processing, explicit consent, data minimization, and the right to erasure. The […]
Read this post