15
+
YEARS OF
EXPERIENCE
1000
+
SUCCESSFUL
Projects
80
+
Satisfied
Clients

In today’s evolving cybersecurity landscape, integrating robust threat detection and response systems is essential for enterprises seeking to safeguard their digital assets. Sentinel Integration with Checkpoint combines Microsoft’s advanced SIEM capabilities with Checkpoint’s industry-leading firewall and threat prevention technologies. This synergy empowers IT teams to detect, analyze, and neutralize cyber threats more efficiently, delivering enhanced visibility and proactive defense mechanisms. In this article, we explore how this integration benefits organizations and the key considerations for seamless deployment.
Enhancing Cybersecurity with Sentinel Integration with Checkpoint
The integration of Microsoft Sentinel with Checkpoint security products enables organizations to unify security event management and sharpen threat detection capabilities. Microsoft Sentinel, a cloud-native Security Information and Event Management (SIEM) solution, aggregates and analyzes security data from various sources, including Checkpoint firewalls. This unified approach helps centralize alerts, automate detection workflows, and supports rapid incident investigations.
Checkpoint’s advanced threat prevention technologies provide granular control over network activities, blocking known and emerging threats at the perimeter. By integrating with Sentinel, security teams gain enriched contextual intelligence and real-time analytics. The data exchange enables automated threat hunting, alert prioritization, and streamlined compliance reporting. This cooperation not only reduces the manual effort required to monitor disparate security platforms but also accelerates incident response times. Leveraging Sentinel’s AI-driven insights with Checkpoint’s comprehensive threat intelligence allows organizations to proactively mitigate risks and ensure business continuity amid an increasingly complex threat landscape.







Key Benefits and Challenges of Sentinel Integration with Checkpoint
Implementing Sentinel Integration with Checkpoint offers numerous benefits, driving efficiency and strengthening security posture for enterprises of all sizes. One of the foremost advantages is centralized visibility across the entire security architecture. Instead of managing multiple fragmented tools, organizations can view all threat-related data in the Microsoft Sentinel dashboard, leveraging powerful search capabilities and customizable analytics.
Automation is another critical benefit. Sentinel offers built-in playbooks and orchestration workflows that can trigger responses based on events captured by Checkpoint firewalls. For example, automated quarantining of suspicious endpoints or blocking malicious IP addresses becomes seamless, freeing valuable security team resources. Moreover, the integration supports compliance with regulatory frameworks by generating comprehensive audit trails and security reports, reducing the risk of fines and reputational damage.
Despite these gains, integrating Sentinel with Checkpoint presents some challenges that organizations must consider. First, appropriate configuration and tuning are necessary to prevent alert fatigue caused by excessive or irrelevant notifications. Security teams need to tailor detection rules and filters to align with their surroundings’s specifics. Additionally, ensuring data integrity and secure communication between Sentinel and Checkpoint devices demands meticulous network configuration and encryption protocols.
organizations must address skill gaps by providing adequate training and documentation, enabling IT staff to fully leverage the integrated platform’s capabilities. Partnering with experienced service providers like TechCloud IT Services L.L.C, trading as Cloud Technologies, can streamline this process and deliver expert guidance tailored to business needs.
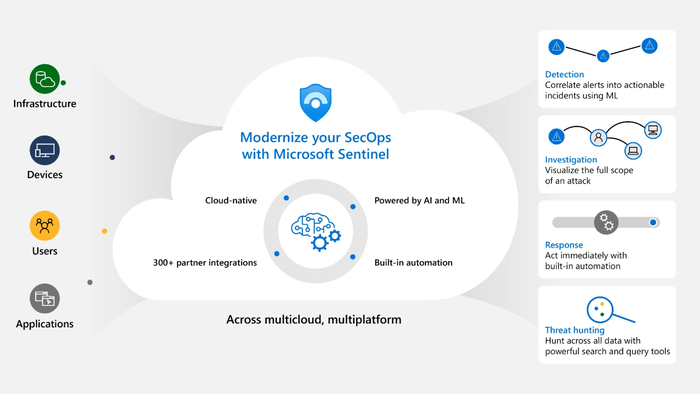
The fusion of Sentinel’s intelligent analytics with Checkpoint’s robust security infrastructure creates a dynamic defense ecosystem. This collaboration allows businesses to optimize their cybersecurity investments by enhancing detection accuracy and reducing manual intervention. With the right configuration, companies can achieve a scalable, adaptive, and resilient security model that keeps pace with evolving cyber threats.
Real-World Applications and Case Studies of Sentinel Integration with Checkpoint
Several enterprises have successfully leveraged Sentinel Integration with checkpoint to transform their security operations. For instance, a multinational financial services firm implemented this combined solution to monitor complex network traffic across multiple global data centers. By aggregating logs from Checkpoint firewalls into Sentinel, the security operations center (SOC) gained unprecedented visibility into lateral movement attempts and suspicious access patterns.
This visibility enabled early detection of malware infiltration attempts and accelerated the response through automated playbooks that isolated affected segments without human intervention. Another case involved a healthcare provider striving to comply with stringent data privacy regulations such as HIPAA. Using Sentinel’s advanced reporting coupled with Checkpoint’s fine-grained policy enforcement, the organization streamlined compliance audits and minimized exposure to data breaches.
These examples illustrate how IT teams benefit from enhanced situational awareness, faster threat detection, and reduction in manual processes. Additionally, Cloud Technologies offers tailored consultancy and implementation services to help enterprises realize these benefits smoothly, ensuring architecture aligns with business goals and security requirements.

answer time
satisfaction
score
on initial call
same business
day
Empowering Organizations Through Integrated Security Solutions
Integrating Microsoft Sentinel with Checkpoint security platforms represents a strategic leap forward for organizations aiming to fortify their cybersecurity frameworks. The seamless fusion of threat intelligence, centralized analytics, and automated response mechanisms enables businesses to stay ahead of emerging threats while optimizing operational efficiency. By partnering with experts like TechCloud IT services L.L.C, trading as Cloud Technologies, enterprises gain access to deep technical knowledge, customized deployment strategies, and ongoing support to maximize this integration’s value.
If you are ready to enhance your security posture and simplify threat management with Sentinel integration with Checkpoint, we invite you to connect with us. Our team of experienced IT professionals is dedicated to delivering tailored solutions that meet your unique challenges and compliance needs. Visit our contact us page today to start the conversation and take the first step toward a stronger, more resilient cybersecurity environment.


