Services
Cloud Technologies - getting
IT done.

Unlocking Network Efficiency with Meraki Best Practices Consulting Cisco Meraki best practices consulting entails a complete approach to designing, deploying, and managing cloud-managed networks to achieve optimal performance and reliability. Cloud Technologies focuses on aligning network architecture with business goals while adhering to Meraki’s recommended configurations. This includes optimal device placement, bandwidth management, security protocols, […]
Read this post
Understanding IT Office Move outsourcing: What It Encompasses and Why It Matters Outsourcing IT office moves involves delegating the planning, coordination, and execution of your technology infrastructure relocation to specialized service providers. This comprehensive service includes inventory management, careful disassembly and packing of hardware, data center relocation, network reconfiguration, and post-move testing. At cloud Technologies, […]
Read this post
Foundations of Best Practices for the SOC Team A strong Security Operations Center relies on foundational best practices that align people, processes, and technology. First and foremost, robust monitoring capabilities are essential. SOC teams must utilize advanced Security Information and Event Management (SIEM) tools combined with threat intelligence platforms to gain extensive visibility into network […]
Read this post
Strategic Benefits of IT Transformation IT transformation offers businesses a strategic edge by enabling agility, scalability, and improved operational efficiency. Modern IT architectures, such as cloud computing and automation, allow enterprises to quickly respond to market demands and reduce time-to-market for new products and services. By transitioning from legacy systems to integrated, flexible platforms, companies […]
Read this post
Understanding the Importance of Secure Infrastructure Management Secure infrastructure Management involves the complete oversight and protection of all IT components-servers, networks, applications, and endpoints-to prevent vulnerabilities and ensure operational continuity. At its core, it addresses risk identification, threat mitigation, system monitoring, and incident response. Modern infrastructures face persistent challenges such as ransomware, insider threats, and […]
Read this post
Why Enterprise 24/7 IT Support Is Essential for Modern Businesses Enterprise 24/7 IT support is no longer a luxury but a necessity for businesses operating in a global and digital marketplace. Around-the-clock IT support ensures that any technical issues, from server outages to cybersecurity threats, are addressed instantly, minimizing disruptions that could result in significant […]
Read this post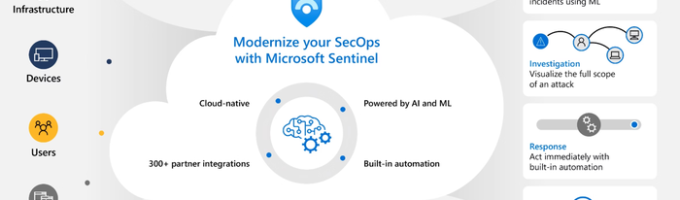
Understanding Microsoft Sentinel Implementation Benefits for Enhanced Security Operations Microsoft Sentinel stands out as a leading cloud-native SIEM and SOAR (Security Orchestration, Automation, and Response) solution that integrates seamlessly within Microsoft Azure environments and beyond. Implementing sentinel delivers significant operational advantages by consolidating security data from a wide array of sources, including on-premises infrastructure, cloud […]
Read this post
Understanding Outsourced Cloud IT Support: A Strategic Advantage Outsourced Cloud IT support involves delegating the management, maintenance, and optimization of your cloud infrastructure to an external expert team. This strategic model allows businesses to access advanced cloud technologies without the need to build or expand in-house IT competencies. Outsourced providers like Cloud Technologies offer extensive […]
Read this post
Understanding the Core Features of Entra ID Network Support Entra ID Network Support provides a comprehensive framework that integrates identity management with network security, ensuring organizations can efficiently manage access controls while mitigating cyber risks. At its core, Entra ID combines centralized user authentication, real-time monitoring, and adaptive access policies to support dynamic network environments. […]
Read this post
Unlocking Growth Potential with MSP for Dubai SME Dubai’s SMEs operate within one of the most competitive and fast-paced business environments globally. For these enterprises, Information Technology is not just a support function-it’s a strategic asset. MSPs for Dubai SMEs focus on delivering customized IT services that empower businesses to streamline operations and reduce downtime. […]
Read this post
Understanding On-Premise Data Migration: A Strategic Overview On-premise data migration involves transferring data, applications, and associated infrastructure from one physical location or system to another within an organization’s local surroundings. Unlike cloud migration, this process is constrained to the company’s private data centers or facilities, making it essential for compliance-heavy industries or those with specific […]
Read this post
Understanding the Importance of Data Migration in Dubai’s Digital Landscape Data migration in Dubai is not simply a technical upgrade; it is indeed a strategic initiative that enables businesses to harness the full potential of digital transformation. Dubai’s rapid growth as a global business hub means organizations require agile IT infrastructures capable of supporting innovation […]
Read this post
Why Upgrading to Microsoft Sentinel is Essential for Modern Security Operations Upgrading to Microsoft Sentinel represents a significant evolution from conventional on-premises SIEM solutions to a fully cloud-native security platform. This transition enables organizations to consolidate all security data from diverse sources, including on-premises devices, user endpoints, and other cloud services, into a single pane […]
Read this post
Understanding Entra ID Security: The Future of Identity Protection Entra ID Security, formerly known as Azure Active Directory (Azure AD), represents Microsoft’s next-generation identity and access management (IAM) platform designed to address contemporary cybersecurity challenges. It functions as a cloud-based service that provides a centralized way to manage user identities, enforce access policies, and secure […]
Read this post
Understanding Cloud Security Services: Foundations for Secure Cloud Adoption Cloud security services encompass a broad range of protocols,technologies,and best practices designed to safeguard data,applications,and infrastructures hosted in cloud environments. These services address vulnerabilities inherent in cloud computing such as data breaches,unauthorized access,and compliance failures. At the core, cloud security involves identity and access management (IAM), […]
Read this post
Overview of Data Migration Services: Ensuring Seamless Transitions Data migration services involve transferring data from one system or storage environment to another, often as part of IT modernization, mergers, cloud adoption, or disaster recovery initiatives. This process is crucial for organizations seeking to leverage newer technologies, improve system performance, or consolidate disparate data repositories. Effective […]
Read this post